BYOD and Data Security: 4 Tips for Mitigating Risks
The availability of new technology, combined with greater workforce mobility, has caused a major shift in the corporate IT landscape. In many organizations, employees can use their personal devices as part of their job. This means that employee-owned mobile devices like smartphones and tablets are increasingly interacting with corporate data.
While deploying bring your own device (BYOD) policies has numerous benefits for both companies and the people they employ, there are also some downsides. The biggest one is the risks businesses face in terms of possible loss or unauthorized access to sensitive corporate data.
This is why any company with a BYOD policy needs to be aware of the security risks it entails and take steps to mitigate them as much as possible. Here are some things your business can do to protect its data from loss or unauthorized access and minimize exposure to common security threats.
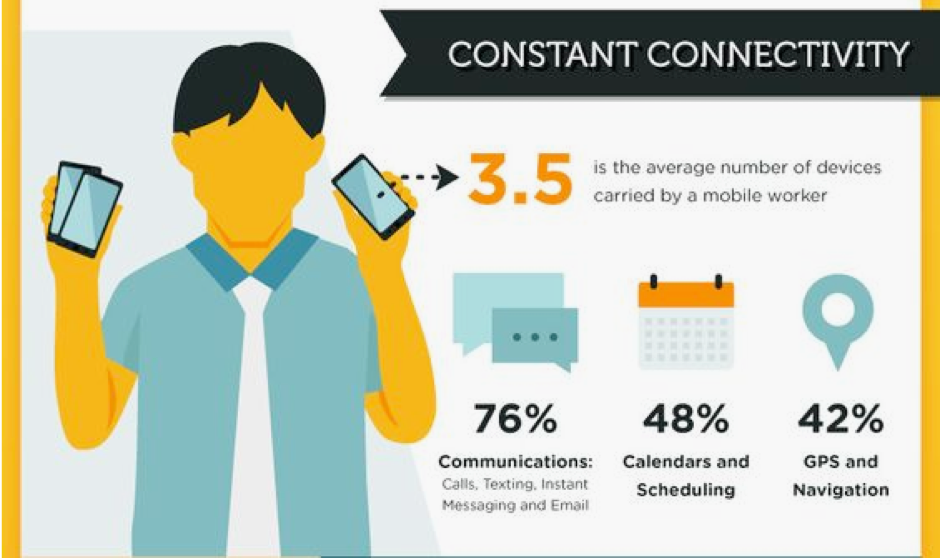
(BYOD cultures allow for greater connectivity for employees, improving productivity and efficiencies. Source: SME Insider)
Set Up a Strong Security Policy
Creating a rigid and comprehensive security policy for your entire organization is the first step to take if you intend to deploy a BYOD policy. Your security policy should outline the rules and procedures everyone bringing their own device to work will have to follow.
Your security policy should address the common risks of BYOD: possible data loss and security breaches. It needs to mandate the use of up-to-date security software on all devices, ensure that all locally-stored data is backed up on a regular basis and include a procedure allowing you to remotely wipe devices that are lost or stolen.
Furthermore, IT security experts recommend restricting the use of jailbroken or rooted devices on your corporate network. While these devices may have increased functionality, they’re also a lot more exposed to security threats. This is due to the fact that they’ve been modified to bypass standard protections offered by the mobile operating system.
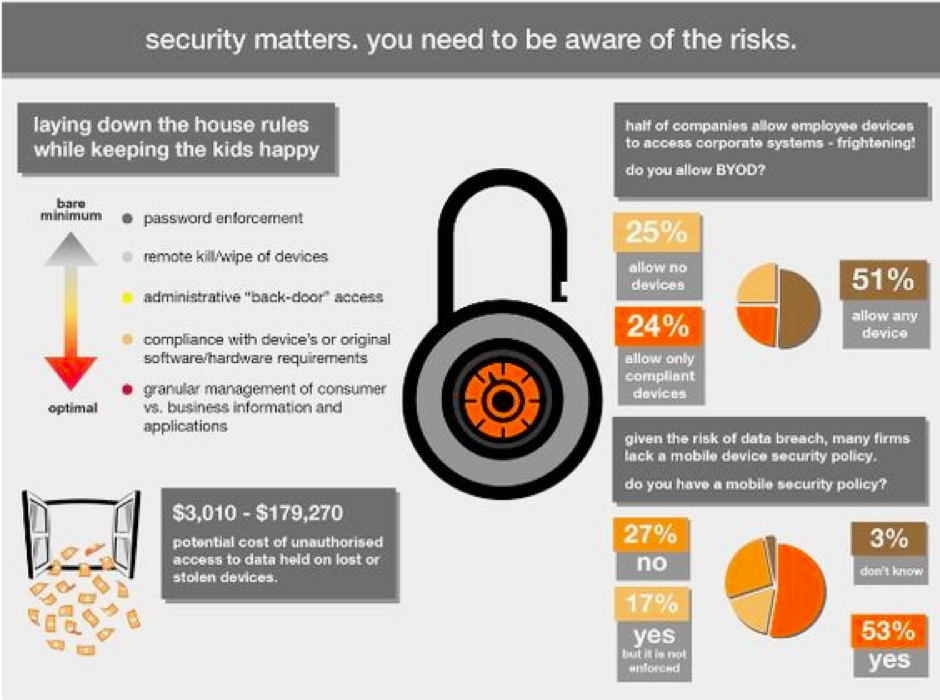
(Take steps to identify and mitigate associated risks for BYOD, including password enforcement and a strong mobile security policy. Source: Evolven)
Train Your Employees
Training and information on security risks associated with using mobile devices is an integral part of any good BYOD security strategy. Employees lacking knowledge of the latest threats may fall victim to hacking attacks and a variety of online scams, which can then result in sensitive company data being compromised.
Many recent security breaches in the corporate are caused when employees access rogue websites or download malicious apps. This enables cybercriminals to use the compromised mobile devices as a gateway to access the corporate network and steal data.
Your employees have to be provided with training sessions and reference materials dealing with a wide range of digital security threats they may face in today’s world. When your company educates its employees about matters such as phishing websites and other online scams, as well as the importance of always using strong passwords, it will reinforce its overall IT security and establish a culture of security across the business.
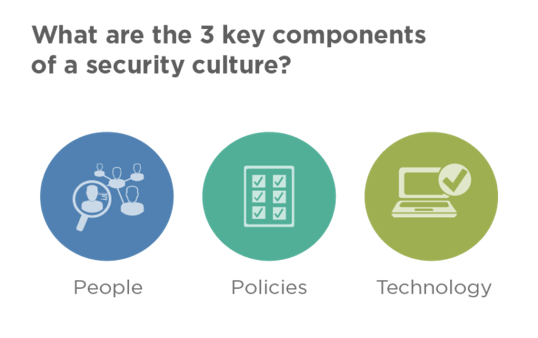
(Ensure you address each of the 3 key components of security in order to guard yourself against risk.)
Prevent Data Leaks
As mobile devices can contain corporate data or have access to resources on the company network, they can become the source of a data leak in case of loss or theft. However, there’s a simple remedy to this security threat: deploy a mobile device management (MGM) system covering all employee devices.
Having a MDM program in place allows administrators to remotely wipe a device in the event that it’s stolen or misplaced. In addition to having a MDM, it is also a good idea for your company to deploy a secure VPN to keep data safe from interception if your employees need access to your network while on the go. This is particularly important if they’ll access data over unsecured public Wi-Fi hotspots, such as those now found in airports, business lounges and hotels around the world.
Provide Support
Your company’s IT support department can help your employees use their devices in a more secure and efficient manner. Support needs to be provided to mobile device users at all stages of a device’s lifecycle, starting from the initial onboarding to decommissioning. A strong support infrastructure will help ensure that all devices are configured properly, have the latest security software installed and are free of potential security vulnerabilities.
Having a comprehensive support strategy in place will reduce potential security breaches in organizations with a BYOD system in place. It can also be very helpful when it comes to increasing overall employee satisfaction with their jobs, as your team members feel like the company cares about them by being ready to address any questions or concerns they have.
Final Thoughts
Having a BYOD policy in your company can bring numerous benefits, such as reducing IT infrastructure costs by allowing staff members to use mobile devices they already own instead of having the company issue them one.
However, there are many security risks inherent to the practice of allowing individual employees to use their own hardware to access sensitive company data. These risks can be mitigated by creating a strong BYOD data security policy that is consistently applied throughout the entire company.
